

One of the most critical components of cyber security is threat intelligence. If we look at the big picture, threat intelligence analysis provides us crucial and aggregated information. This allows for proactive instead of reactive decision making along the way. Let’s briefly look into how we can use threat intelligence to our advantage.
Breaking Down Threat Intelligence:

In a nutshell, senior management and business leaders should be provided strategic cyber threat intelligence that is timely, accurate and actionable. Hence, it is imperative to provide business leaders timely strategic threat intelligence analysis to develop the right cybersecurity policies. As a result of having business leaders onboard allows to fund new projects, tools, training along with staff where required to proactively mitigate threats.
Information – Gather and Correlate
One of the responsibilities of threat intelligence analyst is to gather and correlate data. This information can be gathered from a variety of sources including:
We can then combine these sources to track, target and prevent attacks. We can see how this works in Threat Intelligence Lifecycle.
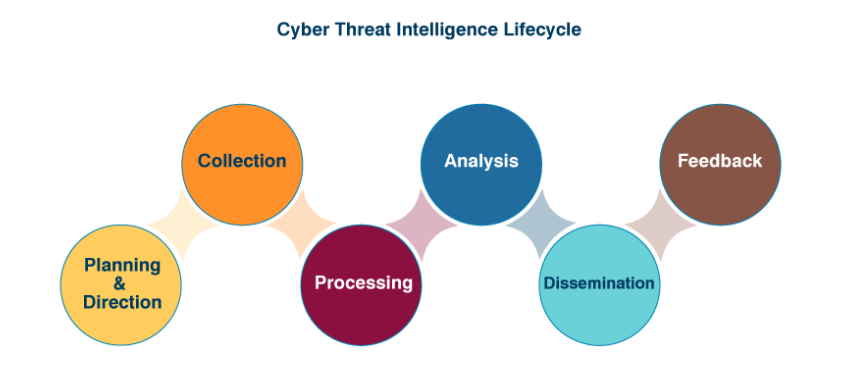
How does Threat Intelligence adds value?
The threat intelligence analyst has to make sure that business leaders understand technical as well as business risks/impact that are involved in addition to plans and strategies that are in place to reduce the risks. Also, it is important to communicate with leadership to invest in the right technologies.
Planning:
Once, all the information is gathered, a plan needs to be created to identify areas to invest the resources. We have to base our plan on authenticity of threats along with how often is it likely to occur. Furthermore, the plan should include investing in skills (people), plans (process) and tools (technology). Then we need to monitor and track things as they are implemented. They need to be aligned with the business objectives of the organization.
Determining the Weakest Links:
There are several ways to determine the weaknesses within the network including conducting penetration testing, vulnerability scans, red teaming and tabletop/walkthrough drills. As a result, all the data gathered empowers leaders to focus on the most important priorities first. This allows the company to have proactive detection, deterrence and remediation of threats. As a result, the organization is more agile. This also increases the trust and confidence between suppliers along with consumer and investors.
Cyberthreat Intelligence Frameworks:
Basically, it focuses attention on the proper areas to ensure follow up, removal and reduction of future threats. Some of the most widely used Cyberthreat intelligence frameworks are:
The cyber threat intelligence landscape is changing by the minute. We have several tactics, techniques and procedures at our disposal to identify and deter/stop attacks from taking place. This also allows businesses to be proactive in their overall approach to prevent future cyber attacks.