

In a nutshell, endpoints are hosts such as laptops, desktops, servers and IP phones and not to mention employee owned devices which generally are referred to as bring your own devices (BYODs). It has almost become a daily occurrence in the news nowadays regarding cyber-attacks on various types of networks especially enterprise networks. If we further investigate these cyber-attacks, they would most likely involve either Distributed Denial of Service (DDoS), Data Breach or some type of Malware.

Endpoints are interconnected by LAN devices such as access points (AP), switches and wireless LAN controllers (WLC). Chances are that most of these LAN devices are prone to LAN related attacks. It is more than likely that malware could strike endpoints via email or web browsing. Furthermore, these endpoints traditionally have been using host-based security features such as antivirus/antimalware, host-based firewall and host-based intrusion prevention systems. These traditional ways of protecting endpoints are obsolete nowadays hence todays’ endpoints are best protected by a combination of an email security appliance (ESA), a network access control (NAC) device and a web security appliance (WSA).
Let’s look at some of these devices in more detail. Just to put things into perspective, email security appliance (content security appliances) include fine-grained control over email and web browsing for an organization’s users. Based on research conducted by Cisco’s Talos Intelligence Group, back in June 2019, over 85% of all email sent was SPAM. The fact of the matter is that phishing attacks occur via SPAM. Furthermore, spear phishing mostly targets senior executives that have elevated login credentials.
Basically, Email Security Appliance (ESA) is a device that specializes in monitoring Simple Mail Transfer Protocol (SMTP). Various vendors have their ESA integrated with real time feeds from their systems which allow them to detect and correlate threats and solutions by using a global database monitoring system. In a nutshell, these ESA perform the following functions:
1. Content encryption in outgoing email to prevent data loss
2. Access blocked to newly infected sites
3. Emails containing bad links discarded
4. Remediate against stealth malware that evaded initial detection
5. Blockage of known threats
The Web Security Appliance (WSA) is also another web-based threat prevention technology. Basically, WSA helps businesses tackle various challenges of securing and controlling web traffic. We look at Cisco WSA for example. It provides total control over how users access the internet. A handful of features and applications such as messaging, video, audio and chat can be allowed, restricted with time and bandwidth limits, or even blocked if the organization desires to do so. Furthermore, WSA can perform the following:
1. Blacklisting of URLs
2. URL-Filtering
3. Malware Scanning
4. URL Categorization
5. Web Application Filtering
6. Encryption and Decryption of Web Traffic
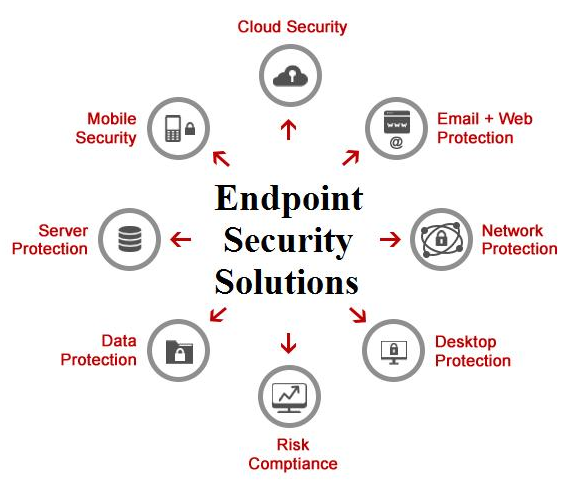
Securing endpoints to their fullest should be an essential part of overall network security design for an organization. Each organization has unique requirements hence it is the job of the entire IT department to decide, implement which devices and services would serve them better. Access Control and Layer 2 security threats are other areas that need to considered as part of securing the LAN and shall be discussed in separate posts. Until then, happy secure networking!