

The role of a network security professional today has become more challenging than ever. Apart from their routine responsibilities to secure the network environments, they are leveraged to support general IT requirements to assist all the folks that are now working from home.
In most of the network implementations, security solutions are configured to protect elements in Layer 3 up through Layer 7 by the the network administrator. Solutions such as IPS devices, VPN and firewalls are used to protect these elements in Layer 3 through Layer 7. Well, why is security of switches that operate at layer 2 so important? This is because if the layer 2 is compromised, the rest of the layers (3 – 7) are also affected by it. To further elaborate on this, if a malicious hacker got access to the internal network and started capturing layer 2 frames, then all security configured on the above Layers (3 -7) would be pointless. Once inside the network, these malicious hackers could cause a lot of damage to networking infrastructure on the Layer 2 Local Area Network.
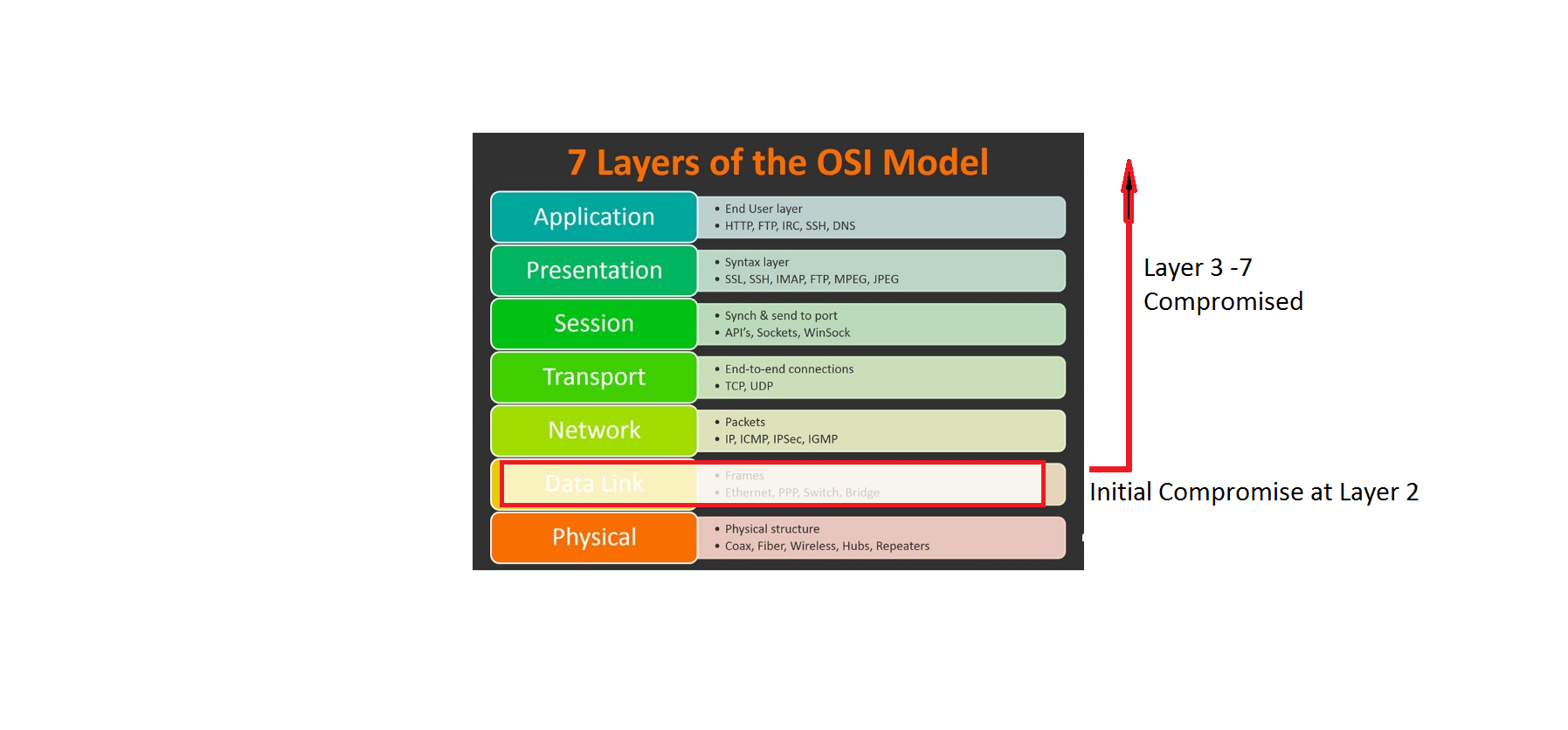
So why are LANs more vulnerable now as compared to years ago? It used to be that before, LANs were traditionally under the administrative control of a single organization. Hence, there was this trust already established between all persons and devices that were connected to the LAN. However, today’s’ LANs are more prone to penetration because of BYOD (Bring Your Own Devices) and sophisticated attacks organized by malicious hackers. As a result, in addition to safeguarding Layer 3 through Layer 7, network security professionals must also protect LAN infrastructure on Layer 2.
Let’s look at some of the known Layer 2 Attacks:
1. MAC Table Attacks: Includes MAC address flooding attacks
2. DHCP Attacks: Includes DHCP spoofing and DHCP starvation attacks
3. ARP Attacks: Includes ARP poisoning and ARP spoofing attacks
4. VLAN Attacks: Includes VLAN hopping and VLAN double-tagging attacks. It also includes attacks between devices on common Virtual LAN.
There are several ways to mitigate Layer 2 Attacks which include:
1. Port Security
2. DHCP Snooping
3. Dynamic ARP Inspection (DAI)
4. IP Source Guard (IPSG)
I will talk in more detail about the Layer 2 attacks and their mitigation techniques in later blogs. As of now, I wanted to give you some idea of what’s at stake here. It is crucial that today’s’ network security professional should take into account all the layers of the OSI model including the overlooked Layer 2 and devices associated with it. Today’s’ threat actors have evolved and have incorporated new and more sophisticated techniques to penetrate networks. Hence the network security professionals today must apply defense in depth approach to further safeguard their network environment.